For too long, cloud security was considered an afterthought or a separate task when operating in or migrating to the cloud. But cloud security should in fact be a core consideration both from the outset and on an ongoing basis.
Organizations that embrace DevOps understand the benefit of moving away from a siloed approach to managing cloud infrastructure. Better collaboration between teams and better visibility for all team members on the end goals mean security can be baked in from day one.
But before we get into the detail of how a DevOps mindset drives more successful cloud security consulting, let's start with some background.
What is cloud security?
There are often misconceptions about cloud security, even within the IT community. Amazon Web Services (AWS), the market leading cloud service provider, uses this helpful graphic to explain the “Shared Responsibility Model”.
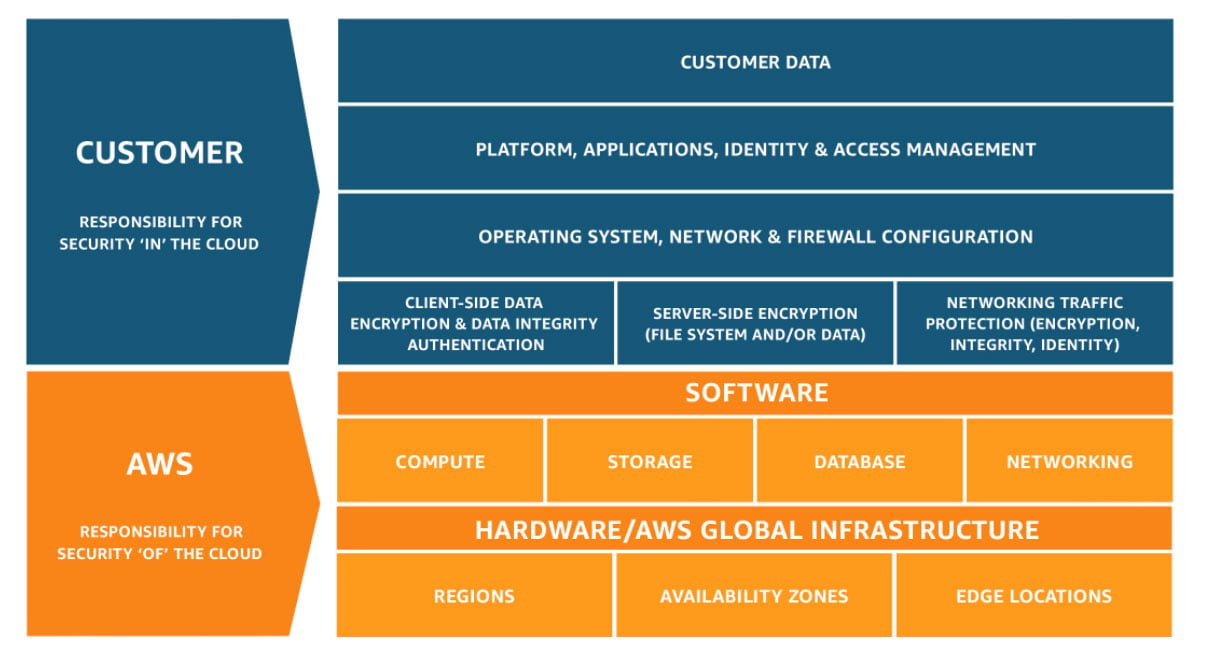
This "Shared Responsibility Model” makes a distinction between security of the cloud environment (the orange layer, AWS is responsible) and security in the cloud environment (the blue layer, you, as the customer, are responsible).
Security of the cloud means protecting the infrastructure that runs the services AWS offers. This includes hardware, software, networking, and facilities that run AWS Cloud services.
Security in the cloud means managing your customer data (including encryption options). You also assume responsibility and management of the guest operating system (including updates and security patches), other associated application software, as well as the configuration of the AWS-provided security group firewall and Identity & Access permissions (IAM).
As AWS puts it: “Customer responsibility will be determined by the AWS Cloud services that a customer selects. This determines the amount of configuration work the customer must perform as part of their security responsibilities.”
Cloud security consulting can help lift or remove the burden of the customer responsibilities. Depending on your skills or needs, a cloud security consultant can help or fully take ownership of the guest operating system, the configuration of the AWS-provided security group firewall and IAM. A consultant can also help you follow best practices for security of application and associated software, encryption and customer data.
But like everything in cloud computing, this consulting work is not a one-and-done situation. Security in the cloud is an ongoing consideration. As your business and your competitive environment change, your cloud security needs will change too.
So while an external partner can support your business in these areas with a one-off engagement, it’s really the ongoing relationships that drive results in the long-term.
What are the top security risks of cloud computing?
You will often hear cloud security consultants use the phrase "security never sleeps". What they mean is the threats to your cloud-based applications don't stop when your in-house team signs off for the day. And those threats are changing all the time.
Here are some examples:
Malicious cyber security threats
New threats constantly emerge from malicious individuals or groups trying to steal personal data from your customers or take control of your systems.
A report by Cybersecurity Ventures, publisher of Cybercrime Magazine, predicted that the global cost of malicious cyber security breaches would reach $8 trillion in 2023 and will grow to $10.5 trillion by 2025.
Organizations need to show the same ongoing commitment to maintaining cloud security as the cyber criminals have to breaching it.
Cloud security and business change
Not all security threats are malicious. A major factor when managing security risk in cloud environments is change.
Businesses use cloud architecture and DevOps methods because of the flexibility and scalability they offer. Innovative businesses want to be able to grow quickly to grab market share or pivot when a new opportunity presents itself.
Cloud infrastructure and a DevOps mindset are great assets in these scenarios. But change brings new cloud infrastructure requirements and new cloud security challenges.
For example, the introduction of a new feature in response to customer demand could require the re-configuration of parts of the infrastructure. This in turn can lead to new types of security risk for the business. One of the most common errors is the misconfiguration of an S3 bucket which could easily lead to exposed customer data.
If security is a separate consideration or a bolt-on afterthought, it significantly impacts business agility. The security team becomes a blocker. But when they are part of the process, they can become enablers.
Cloud security during COVID-19
A more contemporary example of business change is remote working. The COVID-19 pandemic had forced the world into a series of lockdowns, with most workers who weren't furloughed or laid off needing to find ways to work from home.
Across Europe, 40 per cent of people have been working remotely, according to EU figures. And while that's easy and familiar in some cases, in others it is completely new, opening up security risks as employees access systems from different locations and on their own devices.
According to The State of Data Loss Prevention 2020 by Tessian, a cyber security business, more than half of employees admit to shortcutting normal security processes since COVID-19.
With many companies likely to continue with remote and hybrid working models, IT departments will need to adapt their cloud security policies to this new reality.
Human error and cloud security breaches
There is one overarching factor that opens cloud deployments up to security threats. And that is human error.
According to Gartner, the research firm, by 2025, 99 per cent of cloud security failures will be the customer's fault. So while high profile breaches can reflect badly on AWS, Microsoft Azure or Google Cloud, the problem is almost always security in the cloud, not security of the cloud.
Mistakes, oversights and bad configurations by in-house teams are exacerbated by the threats we've already mentioned: malicious hacks or new demands from the business.
Research by Oracle, the US computer software giant, revealed that organizations with multiple mis-configured cloud services had experienced more than 10 data loss events.
The same report revealed that while 75 per cent of firms surveyed felt their cloud deployments were more secure than their own data centers, 92 per cent had a cloud security readiness gap and 59 per cent had had privileged cloud credentials phished.
Cloud security versus compliance
When it comes to cloud computing, your business will face at least some compliance requirements. The number and nature of these requirements will vary depending on where your business operates and what services you offer to your customers.
Getting compliant and staying compliant are both things an external consultant can help you with. But while compliance is vitally important, it is not the same as security.
Just because your business meets the requirements set down by the relevant government agency or industry body it doesn’t mean your cloud deployment is secure. There are two main reasons for this:
Firstly, compliance requirements are slow to change. Standards laid down two years ago might still help to protect your customers from common threats, but they don’t necessarily help you tackle new threats that have emerged in the meantime.
Secondly, compliance requirements are blunt instruments applying to an entire industry or type of activity. They are not unique to your business. But the security issues that cause problems for you and your customers often are.
Compliance should come as a result of good security. Don’t assume good security comes from being compliant.
To get this right, many businesses turn to external cloud security consultants to help them prepare for a compliance audit and to make sure they have the systems and processes in place to remain compliant once they’ve passed.
Just as vital though is the ongoing managed security services that an external consultant can offer to support the creation of an agile, responsive security set-up that goes well beyond the box-ticking approach of meeting your compliance requirements.
Cloud compliance examples
Typically, the compliance requirements for cloud deployments can be split into two parts: legal jurisdiction (national, regional or local laws) and business type (regulations for particular industry verticals or business practices).
Here are some popular examples:
- PCI DSS (Payment Card Industry Data Security Standard): global framework for businesses handling card payments to ensure high standards of data security. More information here.
- HIPAA (Health Insurance Portability and Accountability Act): for U.S. health care and health insurance businesses to protect personally identifiable health information. More information here.
- SOC 1, SOC 2 and SOC 3 (System and Organization Controls 1, 2 and 3): a U.S. reporting structure for internal audits by information services businesses. More information here.
- GDPR (General Data Protection Regulation): EU legislation governing the processing of personal information. More information here.
- ISO 23001 (International Organization for Standardization): global standards for maintaining business continuity, reducing disruptive incidents and improving recovery time. More information here.
Like cloud security, compliance is a moving target. Organizations need to get compliant, but they also need to stay compliant.
That means keeping up to speed with changes in compliance requirements as new rules and frameworks are published. But also being aware of changes to what the business is doing and how those changes might trigger new compliance considerations.
What is a DevOps mindset?
So how does a DevOps mindset help with cloud security? Let's take a step back and look at what we mean by a DevOps mindset.
DevOps is about breaking down the barriers between your development and operations teams. Rather than using a waterfall approach to building software, these teams work together.
Organizations that really benefit from DevOps change not only their processes, but also how they think about their work. Collaboration, shared ownership and iterating often become part of the culture.
This is a DevOps mindset.
What is DevSecOps?
If DevOps is about bridging the gap between two teams (development and operations), DevSecOps is about adding a third team (security) into the mix.
Traditionally the dev team develops a feature, then gives it to ops who give it to the security team before putting it into production. Security is therefore an afterthought.
DevSecOps is about “shifting security to the left” (involving security earlier in the process).
Rather than a separate consideration at the end, security is part of the conversation from the outset. The security team works in close collaboration with development and operations, embracing the principles of agile working processes, regular iterations and focusing on the end result.
"DevSecOps is certainly about security, but it is just as much about the processes you use to build applications and helping to ensure security is built in to those processes by design," said AWS blogger, Steve Andrews. "Think of DevSecOps as putting security in the middle of Dev/__/Ops."
By building and iterating with security in mind from day one, organizations can create more stable, more secure cloud applications.
Research by Google Cloud found businesses that successfully built in security from the start spent 50 per cent less time fixing security issues.
Cloud security consulting: 5 reasons to outsource it
An external cloud security consultant can offer a lot of value when it comes to using DevOps and DevSecOps to operate more successfully in the cloud.
There are useful one-off tasks such as a risk assessment, help creating a robust cloud security policy or penetration testing.
But cloud security consulting can be really impactful when initial assessments transition into ongoing managed security services. Even organizations with large internal teams often choose to outsource in order to get this regular support.
Here are five popular reasons for adding an external cloud security consultant to your in-house team:
1) Cloud security expertise
Cloud computing is so diverse and fast-moving that even well-resourced in-house teams have gaps in their know-how. And while it is tempting to assume these gaps can be plugged as and when they arise, the reality is that lack of expertise is a constant challenge.
It’s true that organizations can experience particular periods of high risk. During the initial cloud migration, for example. Or when rolling out a new product or application. But limited expertise is always a vulnerability.
This issue is one that business leaders understand. A survey of more than 1000 cyber security professionals worldwide revealed security misconfiguration was the top security concern with cloud environments.
Organizations of all sizes have gaps in what their internal teams know, what they’ve done and what they understand. Bringing in external security experts with experience across multiple client projects and cloud deployments can dramatically reduce the risk of major security events occurring.
2) DevSecOps implementation
Embracing DevSecOps requires the proper implementation of processes, tools and automation. This is a big change in how businesses operate and it’s something that needs continuous reinforcement.
As well as changing how they work, teams need to change how they think about their work. This culture change is important because it embeds DevSecOps into the DNA of the organization.
Outside expertise can help organizations with both the initial process of adopting and committing to DevSecOps. And it can provide active, ongoing management and help to reinforce the right processes, tools and mindset, especially when teams grow and bring in new hires.
3) Key person risk
For many organizations, COVID-19 has highlighted how reliant they are on individuals. A global pandemic might mean a key person getting sick, juggling work with childcare or having to work from a new location.
It might also mean that your budget has been cut and you need to find cheaper or more flexible ways to manage your cloud-based applications.
External cloud security experts can often provide that flexibility, with on-demand support to supplement an over-stretched in-house team.
4) Out-of-hours security controls
Security threats can come in the middle of the night, at the weekend or on Christmas Day. Cloud security solutions need to be 24/7/365.
And while automation has a hugely significant role to play in a robust cloud environment, there will always be situations that require human input.
Outsourcing can be a much easier way to provide out-of-hours security monitoring. And it can upgrade and extend your internal monitoring and security strategy, finding and neutralizing threats before they impact business continuity.
5) Ongoing staff training and development
Keeping up with changes in technology and new demands on your cloud infrastructure will put real pressure on your internal teams.
You might have to expand the team to get the right mix of skills. And there is a risk that you will have more than you need in one area and less than you need in another.
An organization's staff members are valuable assets, but they come with costs and liabilities. With cloud computing, there is a constant need to train and up-skill your IT team so your personnel can stay up to speed.
An external consultancy can plug short-term gaps or provide long-term managed services support.
What next?
Cloud security is a big and ongoing challenge for organizations of different sizes and across all industry verticals. Threats from malicious hackers or human error are significant and can cause real financial and reputational damage to your business.
A DevOps approach to security means your organization builds security in from day one. This can dramatically reduce your risk of experiencing security events.
DevSecOps requires new processes, tools and automation, as well as a mindset shift. A specialist cloud security consultancy can provide both the initial support and ongoing managed services to train, upskill and supplement your internal teams.
base2Services is a global cloud delivery and operations company with 15+ years experience helping clients with new and existing cloud migrations. We are strong DevOps advocates and specialize in partnering with clients that want to leverage all the benefits of the cloud.





